Log centralization from different sources
Real-time analysis
Scalable and flexible achitecture to adapt to all needs
Garante Privacy and GDPR compliant


Maximum security in real time
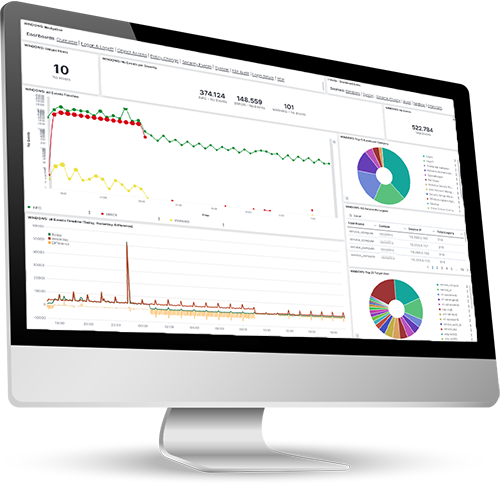
i-Vertix Log & Data Management offers a centralized log management with detailed reporting features and allows to analyse log files in real time through interactive dashboards.
The solutions also provides live information on network traffic and identifies suspicious and dangerous network connections.
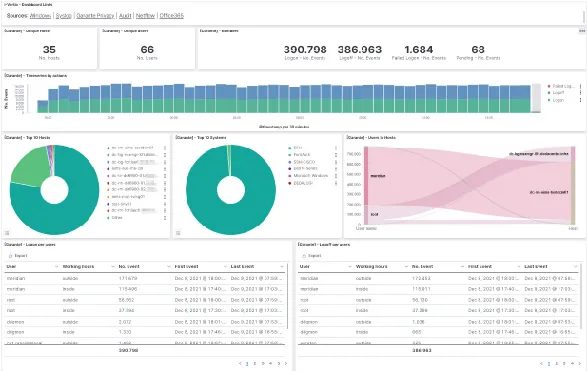

System authentication analysis
- Normalization of the authentication events from several different sources, with immediate and centralized analysis
- Integrations with Syslog, Windows, AS400, WMware and various firewall, network devices e storages
- Compliant with the “Garante della Privacy” and GDPR requirements

Advanced data elaboration
- Real-time parsing and processing of logfiles
- Normalization of the information, to enable comparison between data from different sources
- Log enrichment to add value to the data and allow more targeted analysis

Privacy compliance
- Advanced analysis of massive amounts of information and data inspection through pre configured and customizable dashboards
- Data protection features to guarantee their integrity
- Analysis of custom data coming from applications or systems
Integrated Block List
- Block Lists that contain malicious IPs, dangerous URLs and more
- Early detection of potentially threatening events
An answer to all your needs
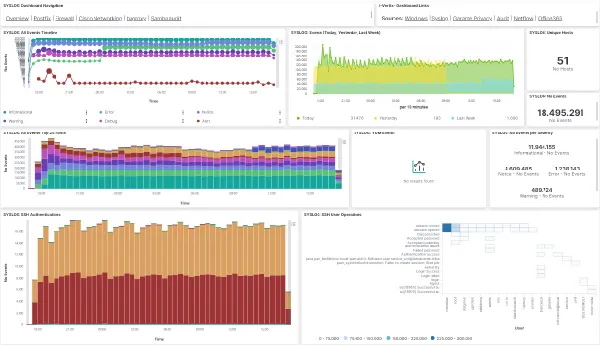
i-Vertix Log & Data Management supports by standard different log file formats, such as those coming from:
- all operating systems
- firewalls
- switches
- web servers
- databases
- applications
Log Management Highlights
Real-time analysis and visualization through pre configured and interactive dashboards
Additional analysis and visualization for data coming from i-Vertix Monitoring
No limits regarding GB/day or events/sec
Creation of alerts from network traffic events (can be combined with i-Vertix Monitoring)
Real-time network traffic analysis to or from potentially threatening sources
Multiple sources that can be configured (including custom)


