SECURITY IS NOT A DESTINATION, IT’S A JOURNEY
How can Netwrix help you ensure that your organization
is more secure tomorrow than it is today?
Pioneering authentication standards for the modern web

IT environments become more complex. Attacks increase in sophistication.
Your teams struggle with disparate tools to manage and secure everything.

Your chances of landing in the breach headlines are skyrocketing.
Eliminate blind spots and overcome complexity
to mitigate the risk of a breach more efficiently.
Netwrix protects the critical information you store — and the vehicles used to get to it — by bridging the gaps between your various security silos. Secure your organization across all the primary attack surfaces: data, identity and infrastructure.
Netwrix | Easy-to-use, strong authentication


A successful journey depends on a good roadmap.
With Netwrix you can build a solid process to guide and measure your progress.
To achieve your security goals, you need a clear and effective strategy. Using a security framework like NIST will help you with every phase of your security journey, and choosing integrated solutions will simplify the work while eliminating blind spots. The Netwrix portfolio addresses all five functions of the NIST framework:
IDENTIFY
Which data is sensitive?
Which accounts pose risk and why?
What gaps leave us vulnerable to threats?
PROTECT
How can we enforce least privilege?
How can we minimize the risk posed by admin accounts?
How can we prevent dangerous changes?
DETECT
Who is accessing sensitive data?
Is there any improper user activity?
Were all configuration changes approved?
RESPOND
Do I have to report a data breach? How can we respond to threats faster? How did an incident occur?
RECOVER
What data needs to be recovered?
How can we revert improper AD changes?
How could an incident have been blocked sooner or prevented altogether?
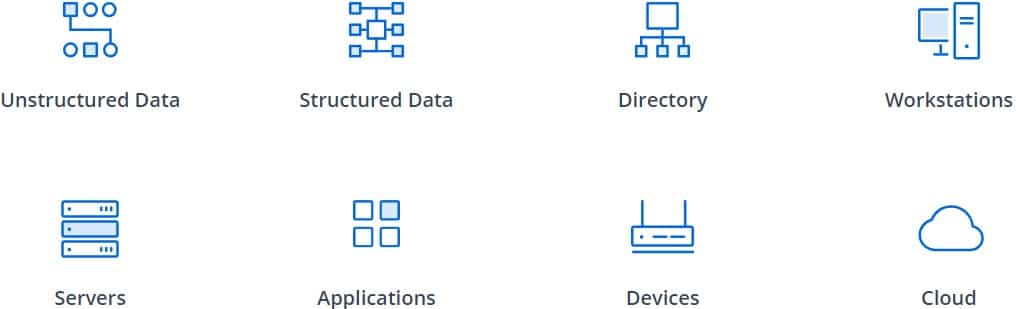
COVER EVERY ELEMENT OF YOUR ENVIRONMENT
Get the comprehensive protection you need
Today’s IT ecosystems are complex, but every element of the environment still needs to be secured and continuously monitored. That includes all the different types of data you store and process, the applications you use, and all your workstations, servers and network devices. Netwrix provides an integrated solution set that covers it all.